Most procure-to-pay (or P2P) failures trace back to unreliable vendor information—unverified bank details, outdated certifications, or incomplete onboarding files. These gaps increase payment errors, disrupt supplier relationships, and weaken compliance readiness. A clear vendor risk assessment framework helps procurement teams eliminate these issues before they escalate.
This article breaks down the risks to watch for and the role Datamatics Business Solutions plays in securing the P2P process.
Key Takeaways
- Vendor risk assessment strengthens P2P security by validating supplier data, preventing payment errors, and ensuring accurate vendor master records.
- Stronger onboarding controls—tax checks, banking verification, sanctions screening, and contract alignment—reduce downstream invoice exceptions and compliance gaps.
- Continuous supplier performance monitoring helps procurement teams detect service degradation early and protect operational continuity.
- Lifecycle-based vendor risk management, supported by Datamatics, keeps certifications, documents, and compliance checkpoints updated, reducing exposure across the supplier base.
Why Vendor Risk Assessment Matters for P2P Security
The health of the P2P process depends on the accuracy and reliability of supplier data. When that foundation is weak, risks multiply quickly. This is why vendor risk assessment plays such a central role in protecting the P2P cycle.
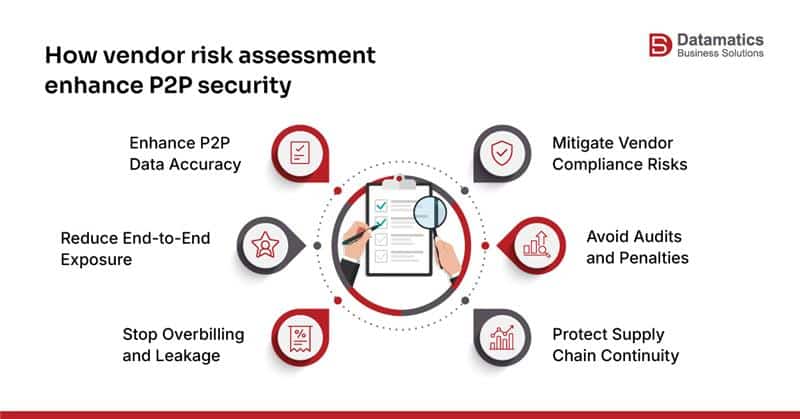
1. Supplier data quality directly impacts P2P accuracy
P2P errors frequently originate from poor vendor master data—incorrect banking information, outdated addresses, missing tax IDs, or duplicate records. Vendor risk assessment ensures:
- Verification of banking and tax information
- Elimination of duplicate vendor records
- Proper classification of supplier categories
- Correct assignment of payment terms
Datamatics BPM supports this through controlled vendor management workflows, banking validations, and role-based access, reducing risk at the source.
You can also read: The Emerging Role of Outsourcing in Sustainability Accounting
2. Financial and compliance exposure often stems From Vendors
Third-party risk assessments are not only cybersecurity risks. For procurement and finance leaders, the more immediate concerns are:
- Unverified supplier tax documents
- Expired certifications
- Regulatory non-compliance
- Inadequate insurance
- Questionable financial stability
A structured vendor compliance management process reduces the probability of audit exceptions, penalties, and supply interruptions.
3. A weak vendor onboarding process slows P2P and increases risk
Vendor onboarding is one of the most sensitive stages in the P2P cycle. When information is collected informally, missing details show up later as invoice exceptions, payment holds, and supplier disputes.
A controlled vendor onboarding process should include:
- Tax and banking verification
- OFAC and basic sanctions checks
- Contract compliance review alignment
- Payment term confirmation
- Clear vendor categorization
4. A weak vendor onboarding process slows P2P and increases risk
Vendor risk is not static. Suppliers may miss deliveries, alter pricing, reduce service levels, or face operational strain. Monitoring performance is a core part of procurement risk assessment.
Datamatics enables supplier performance monitoring through KPI-based scorecards that evaluate:
- On-time delivery
- Quality of goods and services
- Price adherence
- Communication responsiveness
- SLA alignment
This provides early indicators of supplier risk assessment and supports corrective actions.
5. Contract compliance review prevents overbilling and leakage
Contract non-adherence—incorrect rates, missing volume discounts, incorrect freight charges—is a recurring source of leakage. Vendor risk assessment must include a periodic contract compliance review to verify whether invoices match contractual terms.
Datamatics BPM P2P teams support invoice validation, exception handling, and controlled payment runs, creating a closed loop between contract terms and disbursements.
6. End-to-end vendor lifecycle management reduces operational exposure
Vendor risk management extends beyond onboarding. Records require updates, certifications expire, and compliance documents must be refreshed periodically. Many organizations lack the bandwidth for continuous lifecycle management.
Datamatics BPM provides full vendor lifecycle management, including:
- Vendor master updates
- Document expiry monitoring
- Periodic compliance checks
- Risk classification
- Offboarding and archival
This integrated approach maintains P2P integrity and strengthens governance.
How Datamatics Enhances P2P Security Through Vendor Risk Assessment
Datamatics BPM operates as an extension of US procurement and finance teams, providing structured, technology-enabled vendor management across the P2P process. Supported by SOC 1 Type II, SOC 2 Type II, and ISO 27001 controls, Datamatics ensures secure handling of vendor data and financial transactions.
- Vendor management and validation
- Invoice processing and exception handling
- Help desk support for vendor queries
- Payment runs and reconciliation
- Audit support for vendor documentation
This also includes security and compliance controls such as encrypted file transfers, role-based access, DLP and dual-factor authentication, and documented process controls. These controls strengthen P2P security while reducing operational workload for internal teams.
Strengthen P2P Security by Strengthening Vendor Risk Assessment
Vendor risk assessment safeguards the P2P process from financial, operational, and compliance failures. For US procurement and finance leaders managing large supplier bases and demanding audit requirements, reliable vendor assessment is essential. Datamatics provides this foundation through structured vendor management workflows, controlled onboarding processes, lifecycle monitoring, and certified P2P operations.
Connect with Datamatics BPM to streamline vendor management and strengthen P2P security across your organization.
FAQs
1. What does a vendor risk assessment include in a P2P process?
Vendor risk assessment covers financial stability checks, compliance documentation review, supplier performance monitoring, and data validation. Datamatics integrates these controls into daily P2P operations to prevent errors and strengthen security.
2. How does Datamatics BPM improve vendor onboarding?
Datamatics BPM standardizes onboarding with document verification, banking and tax checks, contract alignment, and structured workflows. This reduces downstream invoice issues, payment delays, and compliance risks.
3. Why is supplier performance monitoring important?
Monitoring supplier delivery, pricing, and service levels provides early visibility into potential risks. Datamatics uses KPI scorecards to track performance and support continuous procurement improvement.
4. How does Datamatics BPM support contract compliance review?
Datamatics BPM verifies whether invoices match agreed contract terms, discounts, and pricing structures. This reduces leakage and strengthens vendor compliance management.
5. Are Datamatics’BPM P2P services secure?
Yes. Datamatics BPM operates with SOC 1 Type II, SOC 2 Type II, and ISO 27001 controls, ensuring secure vendor data handling, encrypted transfers, and audit-ready P2P operations.

Ashish Gupta